Cara Unlock Modem Bolt Mf90 Tanpa Dc Unlocker
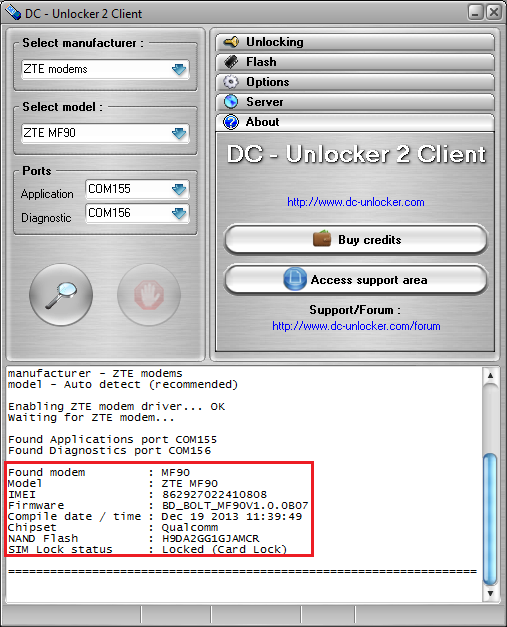
NOTE: This guide is only for ZTE MF90 device with firmware: BDBOLTMF90V1.0.0B08. Unlock procedure is long, at least 10 minutes. Device also can get damaged during unlock for which DC-unlocker is not responsible. Use this unlock method at your own risk.Before unlock steps, make sure you have stable internet connection and electricity source, losing them during unlock process might damage device. Check adapter bindings too like shownOpen ZTE MF90 B08 Indonesia Bolt unlocker softwareIf there is no DC-Unlocker/Rocker/Vygis or Infinity dongle connected to PC, then log in screen will appear. Use your account details to log in, otherwise you have a possibility to access software with free account that will allow you only to detect deviceHow to get username / password seeAfter launching the program, device will be detected automaticallyBefore proceeding further make sure you have stable internet connection, check adapter bindings like shownClick 'Unlock' buttonMonitor the processYou might get error during unlock that drivers are missingOpen device manager and locate your device, it will have '!'
Www.indoblog.me - langsung saja ke inti pembahasan nya bagaimana cara unlock modem zte bolt mifi mf90 mf825a zte mf190 support 4g lte all operator terbaru 2017 unlock modem adalah agar modem bersangkutan yang di lock tersebut bisa digunakan untuk kartu yang lainnya dengan artian karena modem ini merupakan modem khusus untuk kartu Bolt maka agar modem bersangkutan tersebut bisa digunakan untuk. TIPS TRIK UNLOCK MODEM ZTE MF90 (BOLT SUPER 4G) 1. Install DC unlocker versi 1.00.1057 2. Siapkan driver modem ZTE MF90 (sudah diunzip/ekstrak), tanpa perlu diinstall. Hidupkan modem (sudah diisi sim card non Bolt) dengan cara tekan power sekitar 5detik (sampai lampu batre menyala) dan tunggu sampai indikator sinyal menyala.
Mark now next to itRight click on that line and select Update software/driver. Navigate manually to drivers that you have downloaded from top of this guide, mark 'DLOADdrivers' folder and apply. After installation, line that had '?' Should become like shown in image below:If drivers were applied successfully click 'Retry' button on software to finish unlockWait for unlock process to endAfter it finishes disconnect and restart MF90, now it is unlocked and usable with other operator sim cards.REPAIRIf software was closed during unlock process due to any reason and device remained in download mode, then after launching ZTE MF90 B08 unlocker tool, you will need to perform repair in order to unlock it.Open 'Repair' tab on the program. Click 'Refresh' button next to first step. Com port should be detected, if it is, then click 'First step', wait for procedure to finish.
Cara Unlock Modem Bolt Mf90 2018
Click now 'Refresh' next to second step, com port now should be detected there, if it is, click 'Second step' button, new window will open, navigate to directory where ZTE MF90 B08 unlocker software is placed, there you will find DTitems file, select it and click 'Open'. After this repair/unlock procedure will start.
After it is finished, device will be unlocked.
In this tutorial, you will explore how you can use Linux instances to route all your local network traffic with an encrypted SSH tunnel.This tutorial is not meant to be used for routing your server application traffic, but rather to set a VPN-like proxy on your laptop or workstation to bypass certain network limits, such as censorship, and browse the internet privately.This tutorial explores one specific use case of SSH tunnels. For more general information about setting up local port forwarding and other SSH tunnels on Google Cloud, see. OverviewWithout any VPN or SSH tunneling, all your internet traffic goes through your ISP (internet service provider) or any intermediate firewalls your company network might be enforcing. +-+ inspection +-+ Laptop - Internet +-+ firewalls +-+Not only your ISP, other parties who can get in the middle can block your access to websites. They can also inspect and modify the contents of your requests and responses if your connection is not encrypted. For websites, TLS (HTTPs) provides end-to-end encryption.
However not all websites use TLS and not all applications use the HTTP/HTTPs protocols.However, you can host an instance on Google Compute Engine (GCE) and use SSH to create a SOCKS proxy on your machine to make all your traffic go through the instance. +-+ ssh GCE +-+ Laptop - instance - Internet +-+ secure +-+ +-+privateThis way, anyone inspecting your traffic will only see that you are connecting to the GCE instance and GCE instance will forward all your traffic to its actual destination smoothly.This SOCKS proxy provided from the SSH tunnel can later be configured in your operating system as the default proxy and on other applications which have a proxy setting.written by afrizal. LinkBAPIPOSRVAPSSAVEMULTI3DeliveryATP Category BR in APO DRPBAPIPBSRVAPSGETDETAIL2Planning Book dataInput Parameters Planningbook, Dataview, PlanningVersion,PeriodType Values (as in the domain /SAPAPO/CPDSPERIODTYPE e.g. ‘B’ Week ‘C’ Month), DateFrom and DateTo (format e.g.
Ww.yyyy)/SAPAPO/EFPLORDNETGETPegging relationshipFor pegging relationship across the entire strucutureEXIT/SAPAPO/SAPMMCP6005 ZXDMUSERU05User exit macroAdd code in ZXDMUSERU05/SAPAPO/RRPLCPEGIDGETIOMRP Data from Live Cacheto get the data from live cache. Pass the pegid to the export parameter ‘itpegarea’. Determine pegid by using the function module ‘/SAPAPO/DMMATERIALGETPEGID’/SAPAPO/OMPEGCATGETORDERSTo get data from LC at matches the PEGID (= plant, material, storage location) and ATP-categoryYou will just have to specify the ATP-categories that match the MRP elements you would like to retrieve – LC doesn’t store the names of the MRP elements/SAPAPO/OMORDERGETDATAOrder details from liveCacheTo retrieve all information of an order from LC that corresponds to an order id. You just have to use the field ISGENPARAMS-SIMVERSION = ‘000’ and fill the table ITORDER with your order id. If you only want to have the OUTPUTFIXED indicator it would be faster if you use the FM I suggested and then only request ETORDKEY as an output table – this table contains the OUTPUTFIXED indicator/SAPAPO/DMORDKEYSELECTORDNOGUID of Order from liveCacheNeed to provide Order No.
Question: I have a php script on my server that can be execute from the command line and also can be accessed from the browser using Apache web server. I would like to execute execute this php script every 1 hour. How do I schedule this as php cron job on Linux environment.Answer: Use one of the following methods to schedule your php script as linux crontab. A Lot of People have raised queries & are “Genuinely” interested in SIM Card Cloning.Hence, let me explain the Basics:Bottom Line First!:YES, a SIM Can be Cloned. There are Special considerations & Not All SIMs available, can be cloned.You Need Special Hardware. NOT the ordinarily available SIM Reader/Writer.
Network controller driver for toshiba tecra r850. The terms of the software license agreement included with anysoftware you download will control your use of the software. INTEL SOFTWARE LICENSE AGREEMENT (Final, License)IMPORTANT - READ BEFORE COPYING, INSTALLING OR USING.Do not copy, install, or use this software and any associated materials (collectively, the “Software”) provided under this license agreement (“Agreement”) until you have carefully read the following terms and conditions.By copying, installing, or otherwise using the Software, you agree to be bound by the terms of this Agreement.
These “Writers” can ONLY insert SMS & Contacts (.alap). Nothing Beyond That.An Image Below will showcase the Functions that are usually carried out by the across-the-counter available SIM Card Readers/Writers (.alap):The Hardware should be able to write to the EEPROM (or Programmable Memory) of the SIM.Type of SIM:Even though ALL Sims may look alike, the Software (Or in Technical terms: the EEPROM) has evolved (though Slowly) over the years. Reason: Better Reception like 3G & to thwart the efforts of Hackers & Cloners(.alap).(.alap)All-in-All there are FOUR Types of SIM:COMP128v1:These are the Oldest. Commonly available till June 2002, they have little protection. These are the ONLY SIMs that can be Cloned. Hence, if you have a SIM LATER than 2002, STOP Reading ahead. (I know you Won’t, hence.)written by afrizal.
Your +Wordpress user then the following is a list of 15 essential +Plugins that you should install on any wordpress +website.1. +Akismet – For spam protection, make sure you have his key but if you do not have the alternative is a plugin number 22. +Block-Spam-By-Math-Reloaded – Antispam plugin with a simple mathematical method3. +Revision Control – Plugin useful to limit the number of revisions that do not swell your database, go to the Settings - revision - select a maximum of 2 revisions4.
+All in One SEO Pack – Basic SEO Plugin to auto generate custom title and description, after you activate the settings please go to browse titles and descriptions and do not forget the check the auto generated description5. +Simple Social Buttons – Social share buttons simple6.
+Yet Another Related Posts Plugin – Plugin for display the related posts7. +Thank Me Later – Plugin that will send an automated email to the giver first comment8. +SEO Friendly Images – WordPress plugin function to add descriptions to images9. +RSS Footer – Plugin function is to provide a backlink in the footer rss10. +Quick Cache – Plugin cache function to speed up loading web access using the cache system11. +Tweet old post – If you connect with a twitter wordpress plugin use this to promote old posts via twitter12. +Smart 404 – Plugin to display related results when visitors do not find the destination page13.
+Theme My Login – Plugin substitute default wordpress login page14. +Widget Context – Plugin to customize the look of the widget15. +Wordpress Mobile Pack – Display of mobile for your wordpress website16. +Google XML Sitemap – To generate website sitemapwritten by afrizal.